Security
- Multi-Factor Authentication
- Next-Generation End Point Security
- Network Access Control
- Next-Generation Firewall
- Web Application Firewall
- Data Security
Multi-Factor Authentication
.png)
Keep Criminals Outside Your Network with Watchguard AuthPoint
Our unique multi-factor authentication (MFA) solution not only helps to reduce the likelihood of network disruptions and data breaches arising from lost or stolen credentials, but we deliver this important capability entirely from the Cloud for easy set-up and management. AuthPoint goes beyond traditional 2-Factor Authentication (2FA) by considering innovative ways to positively identify users, and our large ecosystem of 3rd party integrations means that you can use MFA to protect access to the network, VPNs, and Cloud applications. Even non-technical users find the AuthPoint mobile app easy and convenient to use!
.png)
Next-Generation End Point Security
Watchguard Threat Detection & Response (TDR)
 Hackers are designing malware to be more sophisticated than ever.
Hackers are designing malware to be more sophisticated than ever. Through packing, encryption, and polymorphism, cyber criminals are able to disguise their attacks to avoid detection.
Zero day attacks and advanced malware easily slip by antivirus solutions that are simply too slow to respond to the constant stream of emerging threats.
Organizations of all sizes need a solution that leverages a holistic approach to security from the network to the endpoint.
WatchGuard Threat Detection and Response (TDR) is a powerful collection of advanced malware defense tools that correlate threat indicators from Fireboxes and Host Sensors to stop known, unknown and evasive malware threats.
Network Access Control

Genians Device Platform Intelligence (DPI), which provides Next-generation device fingerprinting for the IoT era, combines technology information with business context to understand where vulnerabilities may exist. This demands not only a more comprehensive view of the devices themselves but also better understanding of risk indicators.
- Layer 2 based sensing technology for accurate detection of device platform
- Not just “Android phone” but “Samsung Galaxy S6 mobile phone”
- Manage the entire lifecycle of all IP-enabled devices
- Device Platform Identity
- Device Platform Context
- Device Platform Risk
- Expand visibility into IT/OT convergence
- IoT, ICS, SCADA
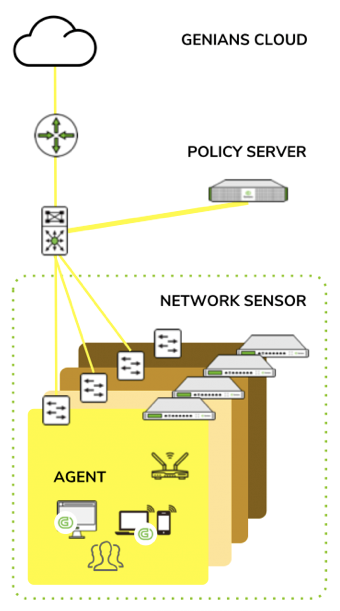
https://www.genians.com/genian-nac/
Next-Generation Firewall
Watchguard UTM Firewall

Watchguard unique approach to network security focuses on bringing best-in-class, enterprise-grade security to any organization, regardless of size or technical expertise. Ideal for SMBs and distributed enterprise organizations, award-winning Unified Threat Management (UTM) appliances are designed from the ground up to focus on ease of deployment, use, and ongoing management, in addition to providing the strongest security possible.
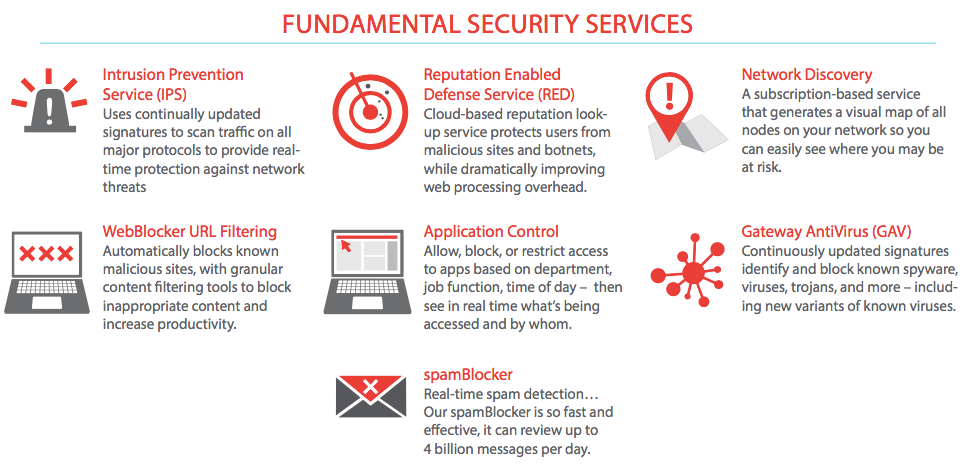
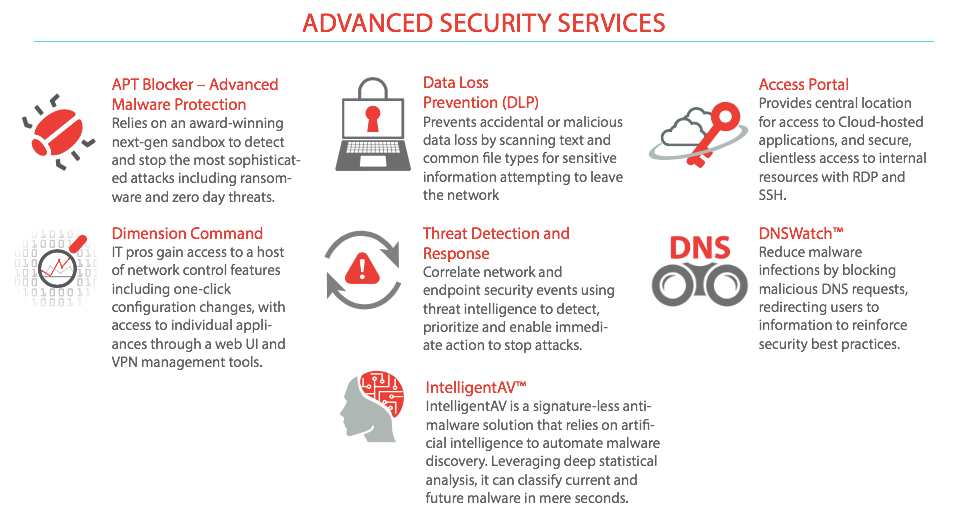
Cisco Security Platform and Next-Generation Firewall
With Cisco integrated portfolio and industry-leading threat intelligence, Cisco gives you the scope, scale, and capabilities to keep up with the complexity and volume of threats. Putting security above everything helps you innovate while keeping your assets safe. Cisco prioritizes security in all that we do. Only with Cisco can you attain effective network security to face tomorrow's evolving threats.
Cisco delivers 3 category of firewalls to Prevent breaches, get deep visibility to detect and stop threats fast, and automate your network and security operations to save time and work smarter. Cisco legacy ASA-series firewall that has proven and well knowns features for the company that looking basic security needs, Cisco Firepower Series that deliver the new advanced protection firewall and Cloud-Managed Firewall that answered by Meraki MX-series.
Checkpoint Cyber Security Products
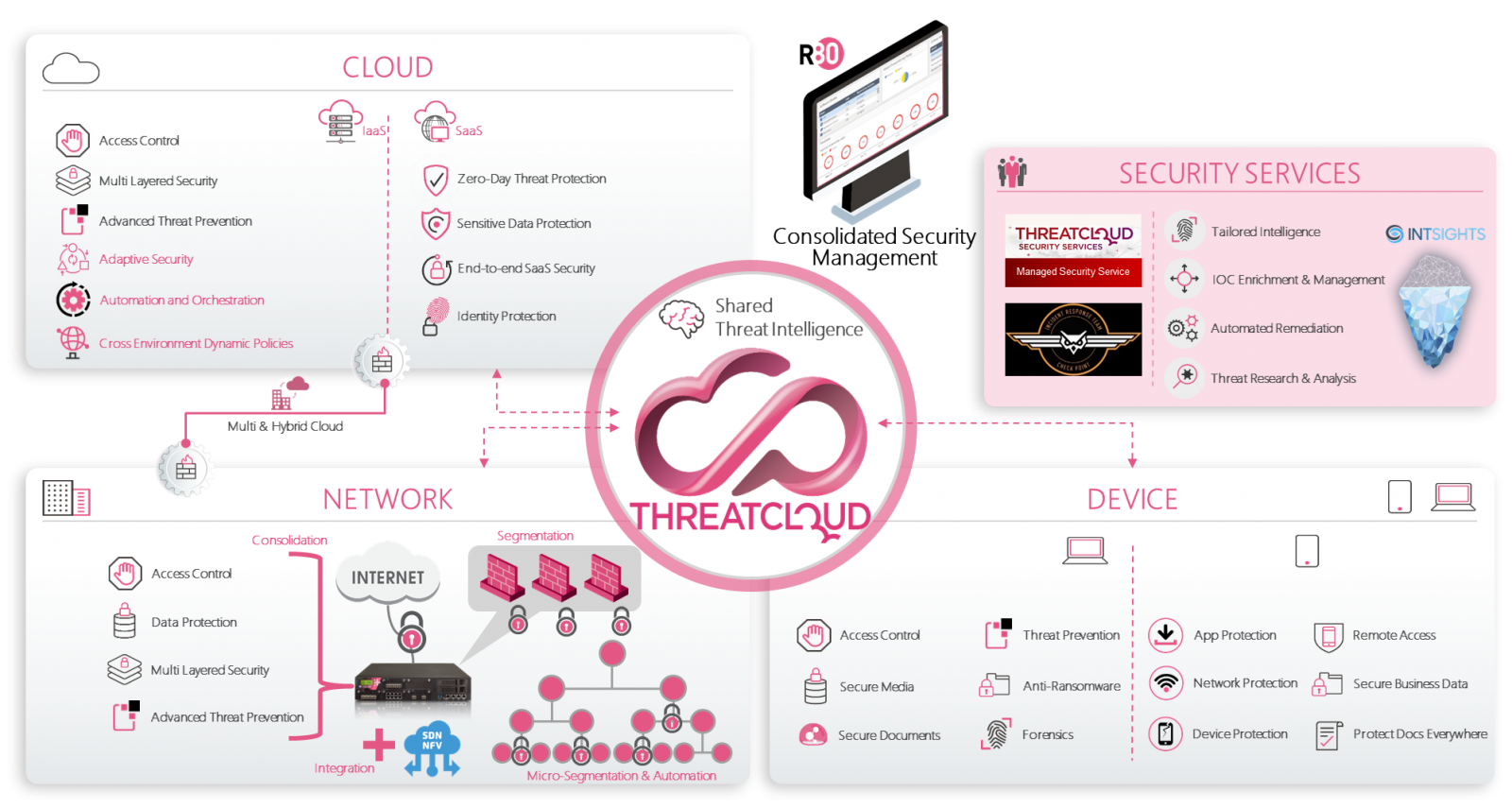
Checkpoint as leader in Security industries that deliver complete end-to-end and On-Premise to Cloud security to enhanced and powered your Enterprise-Grade Security platform.
Check Point Infinity is the only fully consolidated cyber security architecture that provides unprecedented protection against Gen V mega-cyber attacks as well as future cyber threats across all networks, endpoint, cloud and mobile. The architecture is designed to resolve the complexities of growing connectivity and inefficient security, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future.
https://www.checkpoint.com/downloads/products/check-point-infinity-solution-brief.pdf